EXCLUSIVE
Medibank Private – which yesterday announced all 4 million of its customers had been hacked – is running a “not secure” customer login website that has been “exposed and exploitable” for the past five months, according to a top cybersecurity expert.
The “not secure” Medibank “subdomain” – directly connected to the medibank.com.au homepage – has been “exposed” since May due to “basic security oversight and “negligence”, said Cybersec Innovation Partners group CEO Andrew Jenkinson.
Jenkinson said he alerted Medibank to the serious problems late last week – including providing screen shots detailing many of the security flaws – but was told Monday the insurer was “not interested”.
Australia’s biggest private health insurer shed $1.74 billion yesterday, with its shares tumbling 18.1 per cent as trading resumed for the first time in almost a week.
Jenkinson said the exposures included Medibank operating multiple “not secure” websites, including one site using a “not trusted” security certificate, and problems with its PKI, or Public Key Infrastructure, which is used to encrypt data.
The “not secure” subdomain prominently references the “Medibank cyber incident” and links to “important information” about the hack.
It is not known whether the specific security weaknesses identified by Jenkinson were those exploited by hackers – as Medicare is yet to disclose how the breach occurred – but multiple security experts said the basic security flaws highlighted poor security practices by the company.
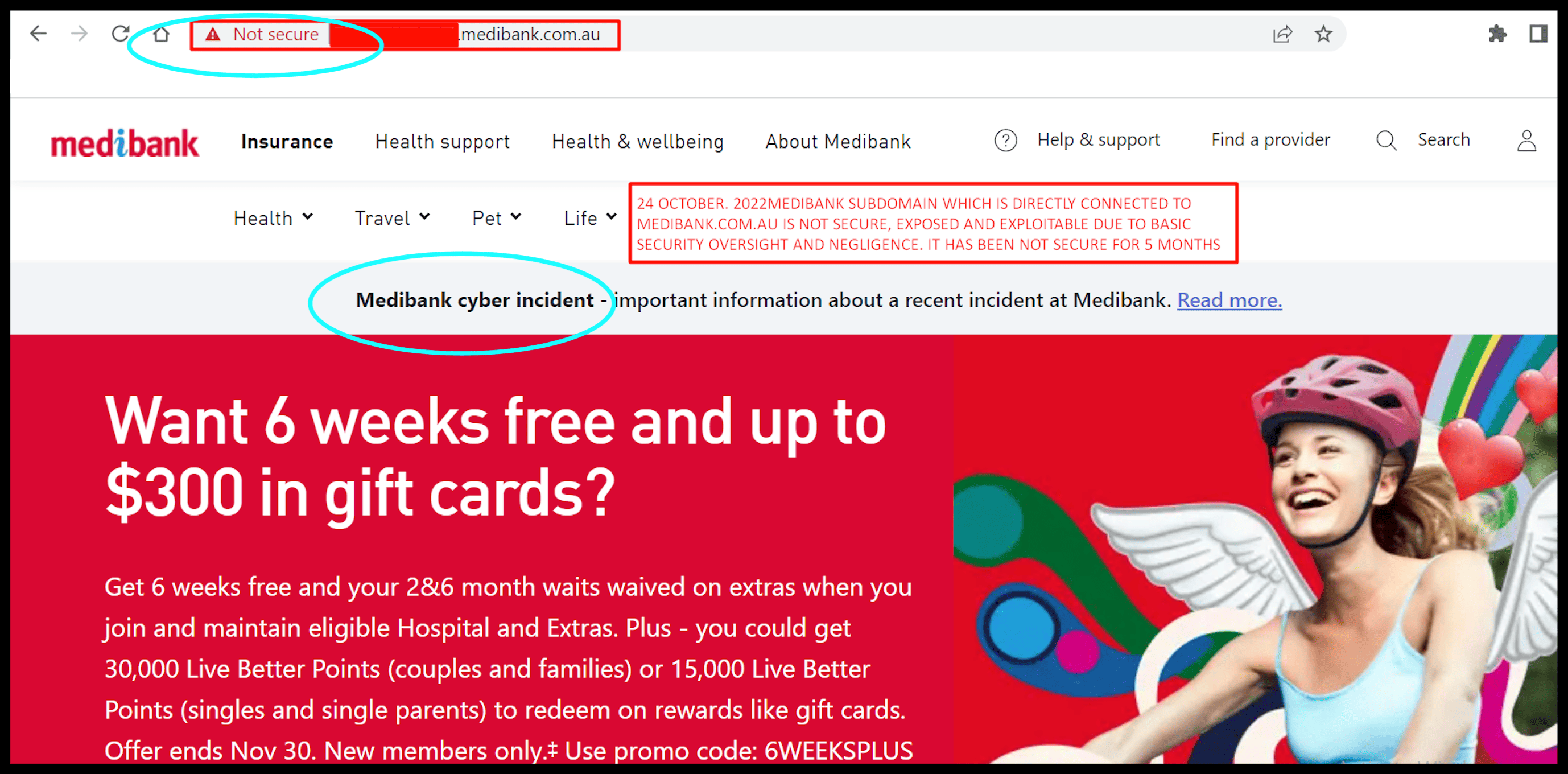
The “Not Secure” Medibank customer site. Source: CIP
All the same problems remained, Jenkinson told The Klaxon on Monday.
“The websites, DNS (domain name system) and PKI issues are ALL still Not Secure,” Jenkinson wrote.
Medibank shares resumed trading on the ASX yesterday, having been suspended for most of the past two weeks, after Medibank on October 13 first cited a problem.
The group has been accused of “drip-feeding” bad news to the market, drawing heavy criticism from some experts.
On October 13 Medibank announced it had “detected unusual activity” on its network but said there was “no evidence” any customer data had been accessed.
The next week, on Monday October 17, it said “there remains no evidence customer data has been removed from the network”.
On Tuesday Medibank announced “a criminal has taken data that now includes Medibank customer data”.
Yesterday it said all 4m of its customers – and an unknown number of former customers – had personal information exposed, including highly-sensitive data about health conditions and medical procedures.
“Our investigation has now established that this criminal has accessed all our private health insurance customers personal data and significant amounts of their health claims data,” said Medibank CEO David Koczkar.
Medi Tank:
Oct 13 – “There is no evidence that any…customer data, has been accessed”
Oct 17 – “There remains no evidence customer data has been removed from the network”
Oct 19 – “Systems have not been encrypted by ransomware”
Oct 20 – “Medibank has been contacted by a criminal claiming to have stolen 200GB of data”
Oct 26 – “The criminal had access to all Medibank customers’ personal data”
Jenkison said he wrote to Medibank director Gerald Dalbosco late last week, including screen shots of Medibank’s “not secure customer website” and other serious security issues, but received no response.
On Monday Jenkinson wrote to Mark Rogers, Medibank group executive, chief financial officer, regarding Medibank’s “exposed and exploitable positions”.
“The attached are examples of lax security, oversight and negligence,” Jenkinson wrote.
“They are examples of how exposed, and exploitable Medibank were, and indeed still are.
Rogers responded on Monday: “Hi Andy, thank you for reaching out, but I’m not interested”.
“Thank you…but I’m not interested” – Mark Rogers
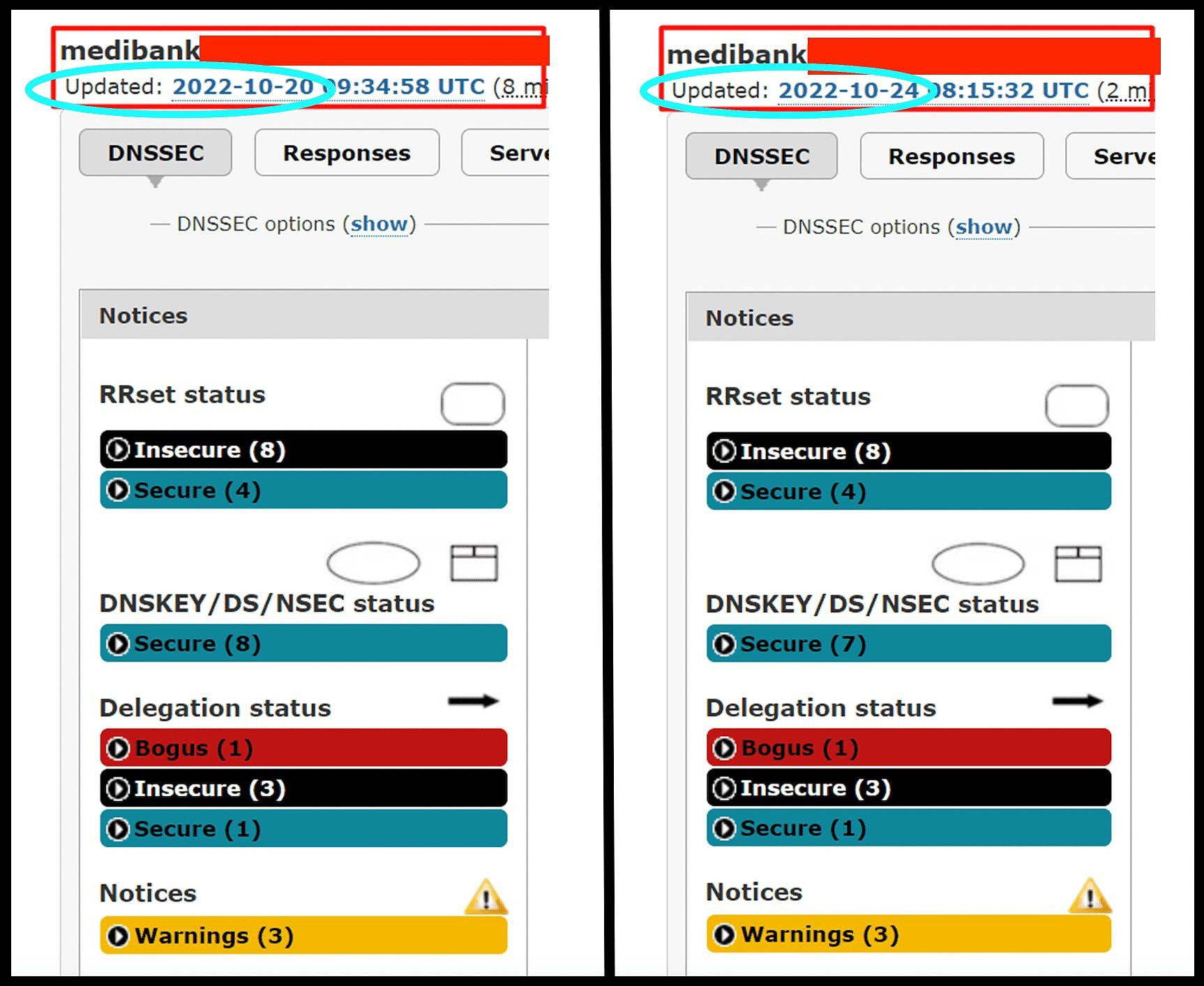
“Insecure” and “Bogus” – Medibank security on Thursday last week (left) and Monday (right). Source: CIP
Jenkinson, who has been global CEO of CIP for the past five years, has authored two books on cybersecurity and managed major projects for UK telco giants BT and Virgin Media.
He is a fellow of the New York-based Cyber Theory Institute (which recently named him the Global DNS Vulnerability expert) and was in January named among the 2021 Top 30 Risk Communicators in Cybersecurity by the European Risk Policy Institute.
Jenkinson has also exposed serious cybersecurity problems at major Australian telco Optus, as revealed by The Klaxon.
Five weeks ago Optus announced personal details of 9.8m current and former customers had been exposed, in one of the nation’s biggest breaches.
On a conference call with analysts yesterday morning, Medibank would not guarantee the hacker or hackers had exited its system.
Medibank technology chief John Goodall said: “It’s an ongoing forensic analysis. Everywhere we’ve identified a breach it’s now closed.”
Medibank shares opened at $3.51 yesterday and closed at $2.87. At 2pm Thursday they were relatively unchanged, trading at $2.88.
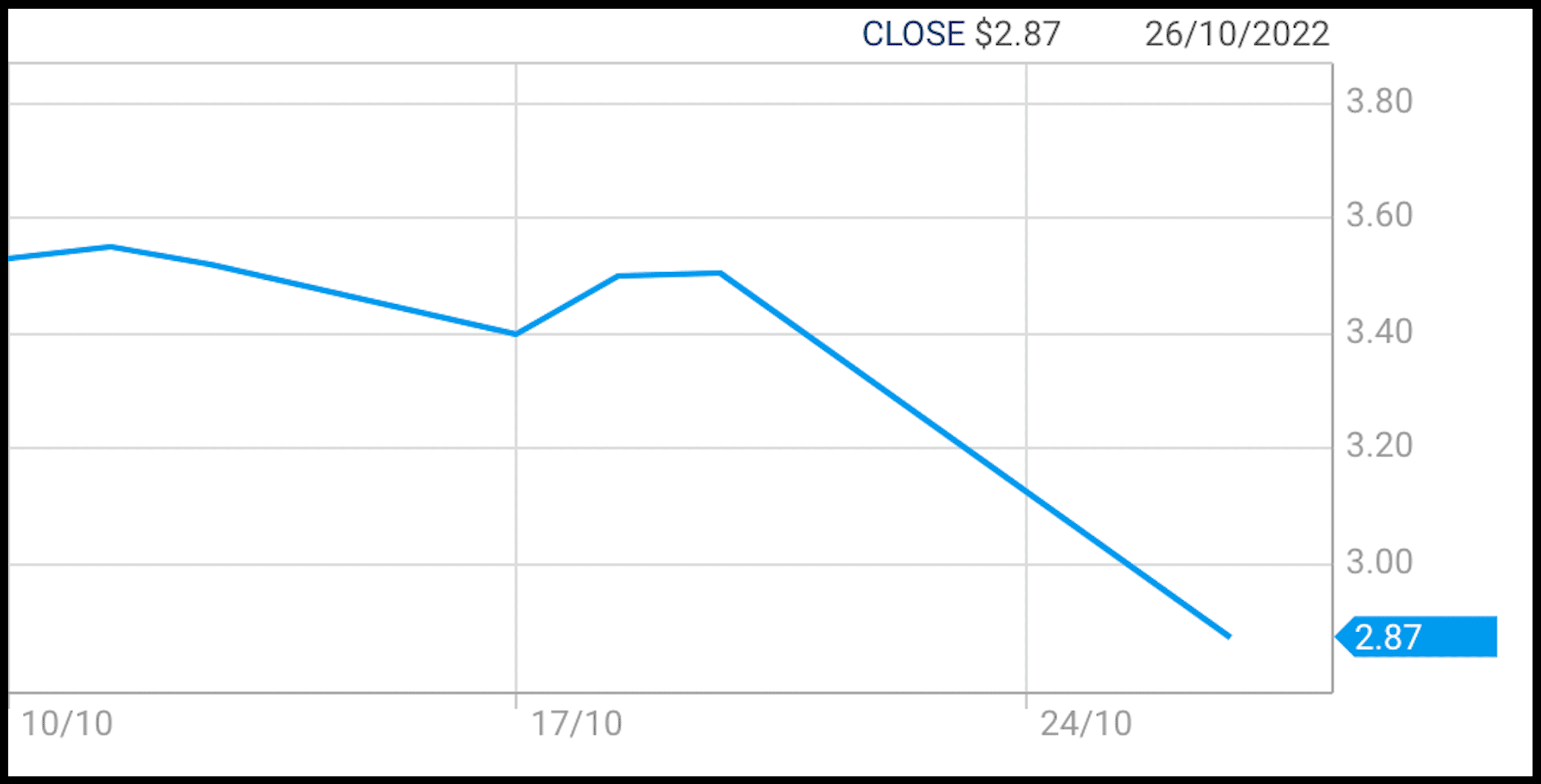
Medibank’s share price at Wednesday’s close. Source: ASX
The group is now Australia’s 66th biggest listed company by market capitalisation, down from around 49th two weeks ago.
In his statement yesterday, Medibank CEO David Koczkar said “The investigation into this cybercrime event is continuing, with particular focus on what data was removed by the criminal.
“As we’ve continued to say we believe that the scale of stolen customer data will be greater and we expect that the number of affected customers could grow substantially”.
WE HAVE A FAVOUR TO ASK: We receive zero government funding and are entirely funded by you – our readers. Please DONATE HERE to support our quality journalism and help keep us afloat.
Help us get the truth out from as little as $10/month.
Unleash the excitement of playing your favorite casino games from the comfort of your own home or on the go. With real money online casinos in South Africa, the possibilities are endless. Whether you’re into classic slots, progressive jackpots, or live dealer games, you’ll find it all at your fingertips. Join the millions of players enjoying the thrill of real money gambling and see if today is your lucky day!
The need for fearless, independent media has never been greater. Journalism is on its knees – and the media landscape is riddled with vested interests. Please consider subscribing for as little as $10 a month to help us keep holding the powerful to account.





