Appreciate our quality journalism? Please donate here
Almost a month after Optus suffered one of the worst data breaches in Australian history the telco giant continues to run “completely insecure” websites with the “weakest, most exposed and exploitable rating possible”, according to one of the world’s top cybersecurity experts.
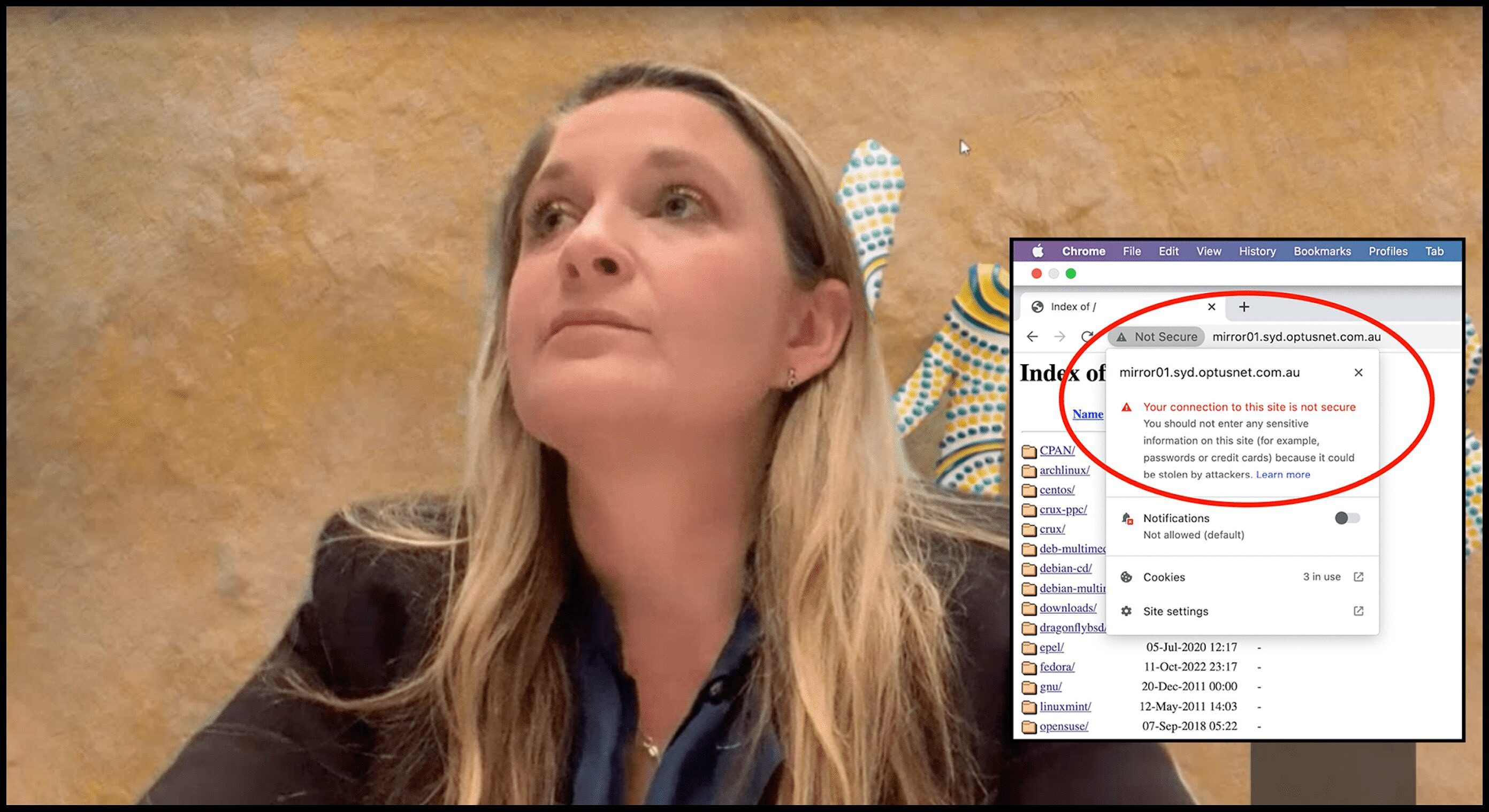
A “sub-domain” run by Optus connects to hundreds of other Optus web addresses, or “URLs”, all of which are deemed “not secure” because they do not have in place security certificates, a simple and standard safety measure.
The sub-domain is a “mirror site”, which are often used by business and other non-consumer customers of IT companies.
“Your connection to this site is not secure,” Google’s Chrome web browser warns when visiting the exposed Optus sub-domain.
“You should not enter any sensitive information on this site (for example, passwords or credit cards) because it could be stolen by hackers,” it says.
“Something is severely wrong with the privacy of this site’s connection. If possible, don’t use the site”.
Other major web browser companies, including Apple’s Safari, Microsoft’s Edge and Firefox, all issue similar warnings. (More below).
A link to the insecure Optus sub-domain was sent to The Klaxon by a concerned reader.
Optus said it provides the site “as part of our telco services as a service to our customers”.
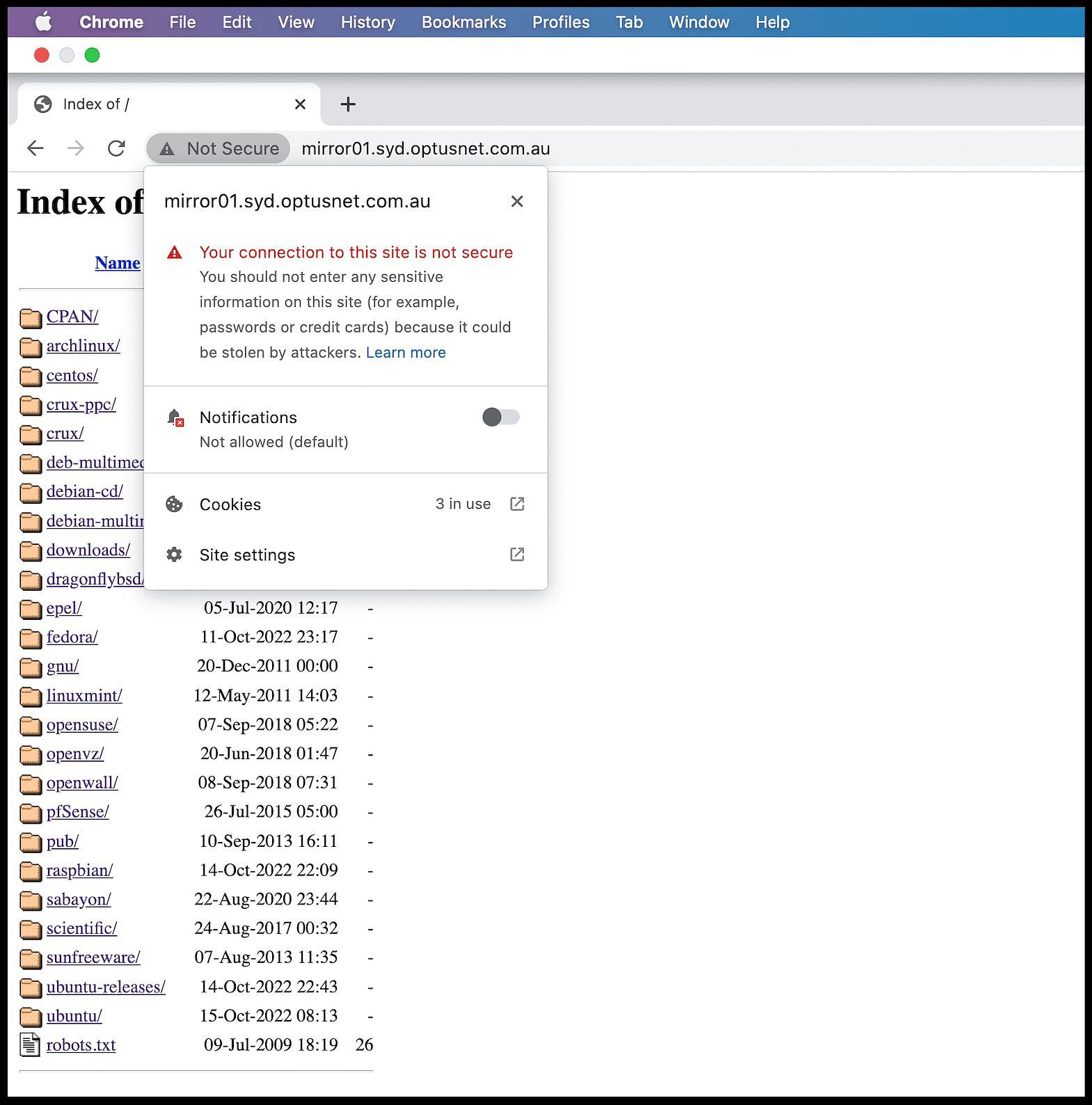
“Not Secure” warns Google’s Chrome browser.
The Klaxon provided the site details to Andrew Jenkinson, CEO of UK-based Cybersec Innovation Partners, who on Friday conducted a security review.
Jenkinson found the sub-domain was “completely insecure”.
A security check revealed the site had a CRI (Cyber Rated Index) of “F & 0”.
“In other words, the weakest, most exposed and exploitable rating possible,” Jenkinson wrote.
“No website should be Not Secure.
“It simply creates opportunity for crime and is very, very poor practice”.
Jenkinson said that fact the sub-domain was a “mirror site” made little difference.
“It is NEVER a good idea to have a Not Secure website,” he wrote.
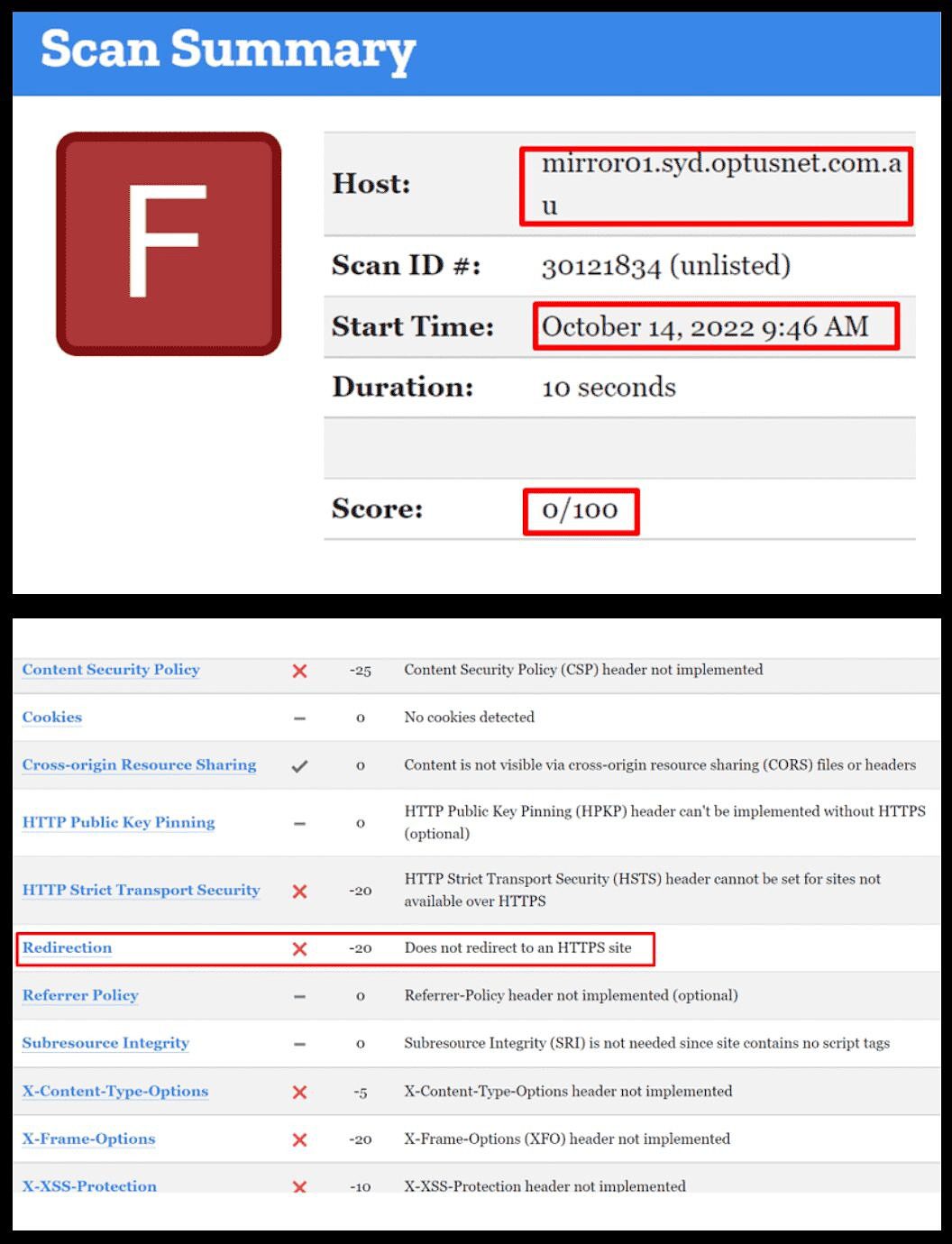
“Score: 0/100”. Part of Jenkinson’s findings. Source: Supplied
Last month it emerged that Optus had been involved in a mass data breach with the personal details of 9.8 million current and former customers stolen, the equivalent of one in two Australian adults.
Optus is owned by telco Singtel, which is majority-owned and controlled by the Singaporean Government.
The Klaxon alerted Optus and Singtel to their “not secure” sub-domain on Friday, and that experts had warned it presented a major security weakness.
The group rejected there was a problem.
In response to questions put directly to each Optus CEO Bayer Rosmarin and to Singtel chair Lee Theng Kiat, The Klaxon received a statement saying the site “does not represent a major security weakness”.
“This website is a public filesharing mirror, intentionally open for sharing open source files which we provide as part of our telco services as a service to our customers,” said a statement from the group.
“Other service providers across Australia (and the world) do the same thing.
“This does not represent a major security weakness,” it said.
Jenkinson, who has been group CEO of Cybersec Innovation Partners since 2018 and has written two books on cybersecurity – Stuxnet to Sunburst, 20 Years of Digital Exploitation and Cyber Warfare and Ransomware and Cybercrime, published in July – rejected Optus’ claims.
“It’s quite laughable the response they have given you,” Jenkinson wrote to The Klaxon.
“Whomever answered your question and sent that response either did not realise the website is Not Secure or DOES NOT have a good comprehension of Internet Security and website security.
“It’s quite laughable the response they have given you” – Andrew Jenkinson
“Furthermore, whomever is connecting and modifying the content are doing so without realising the website could be being used for nefarious purposes”.

CIP group CEO Andrew Jenkinson. Source: Supplied
Jenkinson is a fellow of the New York-based Cyber Theory Institute, which recently named him the Global DNS Vulnerability expert.
He has managed major projects for telco giants British Teleco and Virgin Media, and sits on the International Advisory Council of the Human Health Education and Research Foundation (HHERF).
In January he was named among the 2021 Top 30 Risk Communicators in Cybersecurity by the European Risk Policy Institute.
“It really is quite distressing to see such level of ignorance” – Andrew Jenkinson
Websites with valid security certificate show the letters “HTTPS” at the start of their URL, rather than simply HTTP.
HTTPS, which stands for Hypertext Transfer Protocol Secure, is the secure version of HTTP.
HTTPS started gaining widespread traction in 2016 and has been considered essential by cybersecurity experts and internet browsing companies since 2018.
“These days, installing a (safety) certificate on your site is a must,” as it “protects your data as it travels between your site and the server,” says major cybersecurity firm Sectigo.
“When a website says not secure it can have serious consequences.
“Insecure websites are vulnerable to cyberthreats, including malware and cyberattacks.”
Jenkinson said there was a misconception among some in the IT industry that having exposed “mirroring” sites, such as the Optus sub-domain, was not harmful.
“It is NEVER a good idea to run HTTP period,” he wrote.
“By doing so it can enable attacks and redirections without controls and governance.
“Let me repeat for the avoidance of doubt, It is NEVER a good idea to have a Not Secure website.
“Anyone who has an opinion that it is okay is simply incorrect and not thinking of all the illegal actions that can take place,” Jenkinson said.
“Anyone who has an opinion that it is okay is simply incorrect” – Andrew Jenkinson
Jenkinson said in 2018, “after four years of consultation, Google and the industry migrated from HTTP to HTTPS”.
“Google were so angry at the lack of adoption that they said they would name and shame those that DID NOT take security seriously by displaying a Not Secure text in the URL,” Jenkinson wrote.
Google’s Chrome started rolling-out “not secure” warnings on some non-HTTPS sites in 2016.
In July 2018 – over four years ago – it announced that all non-HTTPS sites would be marked “not secure”.
Three months later it went a step further, showing a “red warning”.
“In October 2018, we’ll start showing a red “not secure” warning when users enter data on HTTP pages,” Google Chrome said at the time.
Peak international digital security group the Electronic Frontier Foundation (EFF) says “HTTPS provides the baseline of safety for web application users”.
“Web application providers undermine their business models when, by continuing to use HTTP, they enable a wide range of attackers anywhere on the internet to compromise users’ information.
“There is no performance or cost-based reason to stick with HTTP,” it says .
“There is no performance- or cost-based reason to stick with HTTP” – EFF
The mass Optus breach was announced on September 22.
The Australian Government’s top cybersecurity agency, the Australian Cyber Security Centre (ACSC), conducted a week-long technical review, which Cyber Security Minister Clare O’Neil announced as complete on October 1.
It was a “basic hack”, O’Neil says, with Optus having “effectively left the window open for data of this nature to be stolen”.
O’Neil and the Federal Government have consistently and firmly stood by that appraisal.
By contrast, Optus CEO Kelly Bayer Rosmarin has stated, repeatedly, that the mass breach was a “sophisticated attack”.
She has provided no evidence to back her claims.
On October 3 Bayer Rosmarin announced a “review” into the breach by consultancy Deloitte, but has said the findings will be kept secret.
Rosemarin and Singtel’s governance arrangements have repeatedly come under serious scrutiny, including after Bayer Rosemarin announced in February she had appointed to a senior role former NSW Premier Gladys Berejiklian, who was at the time, and remains, the subject of unresolved corruption investigations.
How The Klaxon broke the Trustwave story, October 10. Source: The Klaxon
Last week it emerged another Australian-based arm of Singtel, major IT firm The Dialog Group, had been hit with a data breach affecting “1,000 current Dialog employees as well as former employees” with data published on the dark web.
As many as 20 clients of its clients were also affected. As previously reported, the company lists 36 clients on its website.
Among them are over a dozen government agencies, including Centrelink, the NSW Electoral Commission, and Queensland Health.
The Klaxon a week ago revealed Optus owns and operates, along with its parent Singtel, a “world-class” global cybersecurity arm, Trustwave, which has “over 200,000 business and government customers” in “96 countries” – but is refusing to say whether it was being used to protect the 9.8m consumer customers whose data was exposed.
No other Australian media outlet has covered the story.
Security Suite
The most used browsers worldwide are Google’s Chrome, with almost two-thirds of the market (65.7%); Apple’s Safari (18.7%); Microsoft’s Edge (4.3%); and Firefox, owned by not-for-profit Mozilla Foundation (3.1%).
Together they represent 91.8% of the market, says web analyst Statcounter.
The Klaxon has accessed the Optus site using each of those browsers.
They all warn it is “not secure”.
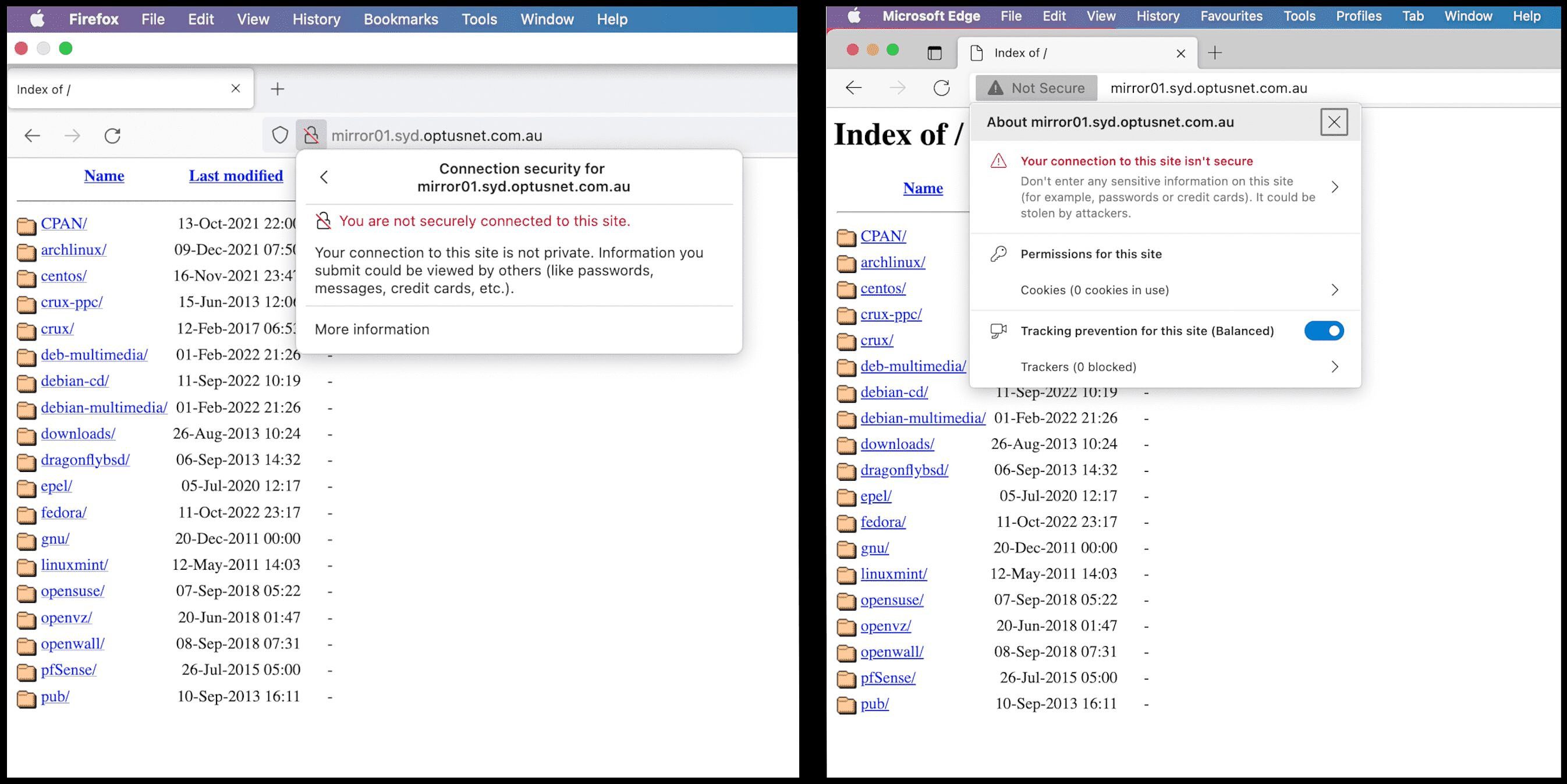
The Optus sub-domain accessed via Firefox (left) and Microsoft Edge (right). Source: Optus
The Optus site was “last modified” by a user today, October 17, at 11.51am.
At time of publication it remains live and “not secure”.
The sub-domain links to hundreds of other Optus “sub-directories” and thousands of files.
One sub-directory, dated May 2013, is named “sevcuritysuite”, and links to a series of security programs dating as far back as 2008.
It links to “Optus Internet Security Suite” installable programs, labelled “OISS 2008 Installer”, “OISS 2009 Installer” and “OISS 2010 Installer”.
Optus continues to operate its “Optus Internet Security Suite”, for which it charges $6.99 a month, a document dated August 22 shows.
The Optus sub-domain. Source: Optus
Safety certificates, or SSL certificates, are used to and authenticate a website’s identity and issued by many cybersecurity companies.
Web browsing companies determine whether a a site’s safety certificate comes from a reputable provider, that it is valid and not expired.
If these conditions are not met – or a site has no certificate in place at all, like the Optus sub-domain – then it is flagged “not secure”.
Safety certificates enable encrypted connections so as to prevent “criminals from reading or modifying information transferred between two systems”.
The week after Optus announced the mass data breach – and after the Federal Government said it was a “simple hack” – Bayer Rosmarin hit out at “misinformation”.
“Our data was encrypted,” she said.
That has been disputed by multiple experts.
Former head of the Federal Government’s Australian Cyber Security Centre, Alastair MacGibbon has said that description represented a “word salad” because the Optus data appeared to have been unencrypted when it reached the hacker.
“When you load a website over plain HTTP, your connection to the site is not encrypted” warns Google’s Chrome.
“Chrome’s ‘not secure’ warning helps you understand when the connection to the site you’re on isn’t secure and, at the same time, motivates the site’s owner to improve the security of their site”.
WE HAVE A FAVOUR TO ASK: We receive zero government funding and are entirely funded by our readers. Our financial position is currently extremely tight. If you appreciated this article, and our high-quality investigative journalism, please DONATE HERE to help keep us afloat. Thank you very much for your support.
Anthony Klan,
Editor The Klaxon
Help us get the truth out from as little as $10/month.
Unleash the excitement of playing your favorite casino games from the comfort of your own home or on the go. With real money online casinos in South Africa, the possibilities are endless. Whether you’re into classic slots, progressive jackpots, or live dealer games, you’ll find it all at your fingertips. Join the millions of players enjoying the thrill of real money gambling and see if today is your lucky day!
The need for fearless, independent media has never been greater. Journalism is on its knees – and the media landscape is riddled with vested interests. Please consider subscribing for as little as $10 a month to help us keep holding the powerful to account.