Appreciate our quality journalism? Please donate here
EXCLUSIVE
Telco giant Optus runs a “world-class” global cyber security business – bought for over $1 billion in 2015 – but is refusing to say whether it was used to protect its Australian customers, the group’s biggest source of profit.
As Australia reels from one of the biggest data breaches in its history – with authorities facing reissuing over two million drivers licences, Medicare cards, passports and other government identification documents – it can be revealed Optus claims to be a “global cybersecurity leader”.
Optus’s “award-winning threat research and intelligence” arm, Trustwave, provides “government and business” clients with “elite cyber security expertise” to “eradicate cyberthreats with world-class intel and expertise”.
“We provide managed security services and consulting services and technologies to the largest global brands, helping them embrace digital transformation securely,” says Optus.
“Tap into our global team of tenured cyber security specialists…(and) eradicate cyberthreats with world-class intel and expertise”.
“Eradicate cyberthreats with world-class intel and expertise” – Optus
Trustwave, the “global security arm of Singtel, Optus and NCS”, has “200,000+ business and government customers”, providing its “award-winning”, “elite cybersecurity expertise” across 96 countries.
The personal details of 9.8 million current and former Optus customers – about one in two Australian adults – were exposed in the mass breach, which emerged two-and-a-half weeks ago.
The scandal has dominated Australia’s media cycle, spawning hundreds of articles, yet until now it appears not one report has identified that Optus owns, runs and heavily spruiks – at least to third-party business and government customers – Trustwave, its own global cybersecurity giant.
Singaporean Government-controlled Singtel, which owns Optus, bought Trustwave seven years ago for US$810 million ($1.243 billion) and established Trustwave as “the global security arm of the group”.
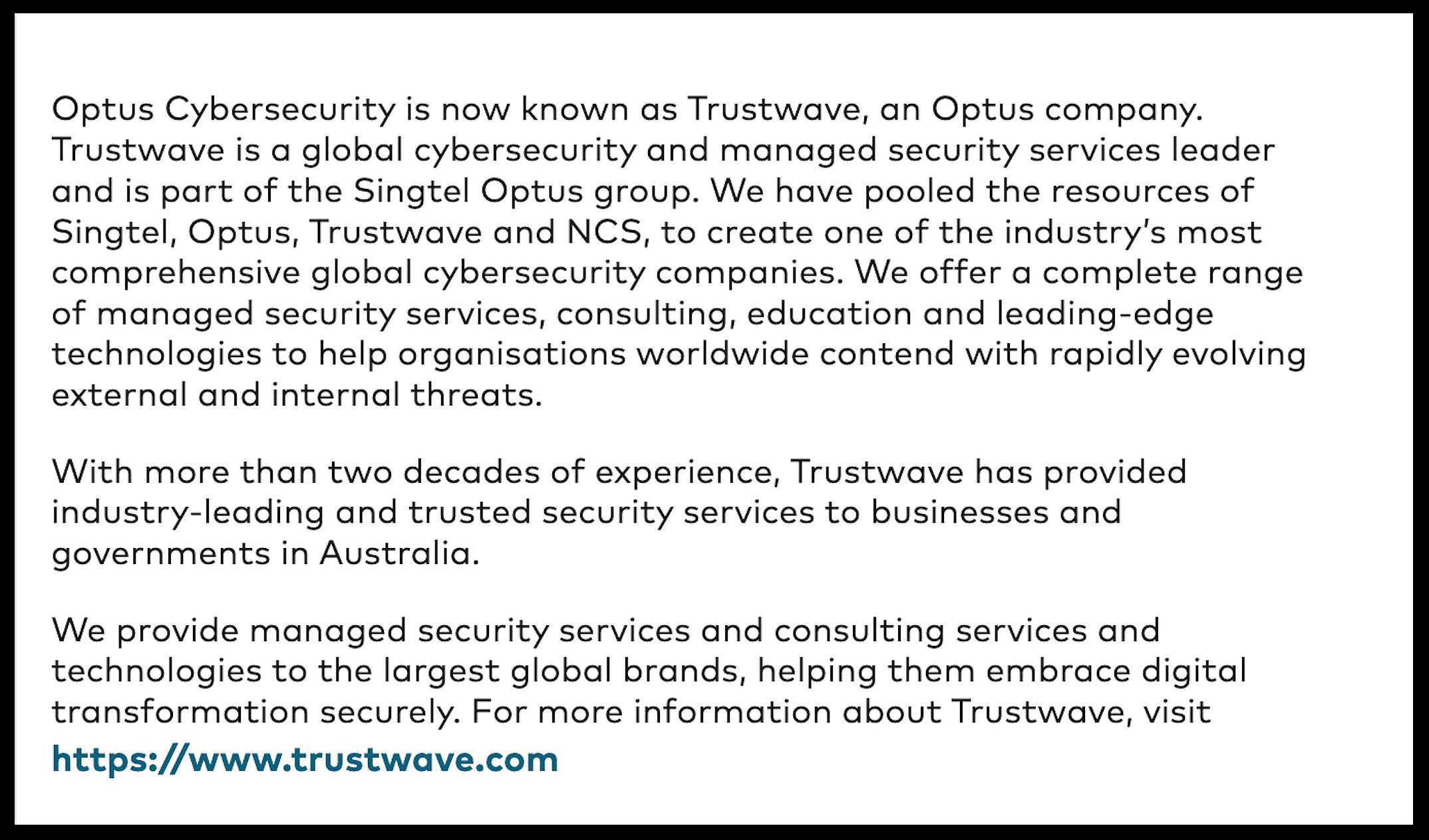
“Optus Cybersecurity is now known as Trustwave, an Optus company,” says the Optus website.
“Optus Cybersecurity is now known as Trustwave” – Optus
“Trustwave is a global cybersecurity and managed security services leader and is part of the Singtel Optus group.

“Trustwave, an Optus company”. Source: Optus
It had “pooled the resources ” of Singtel, Optus and Trustwave “to create one of the industry’s most comprehensive global cybersecurity companies”.
“We offer a complete range of managed security services…and leading-edge technologies to help organisations worldwide contend with rapidly evolving external and internal threats,” Optus says.
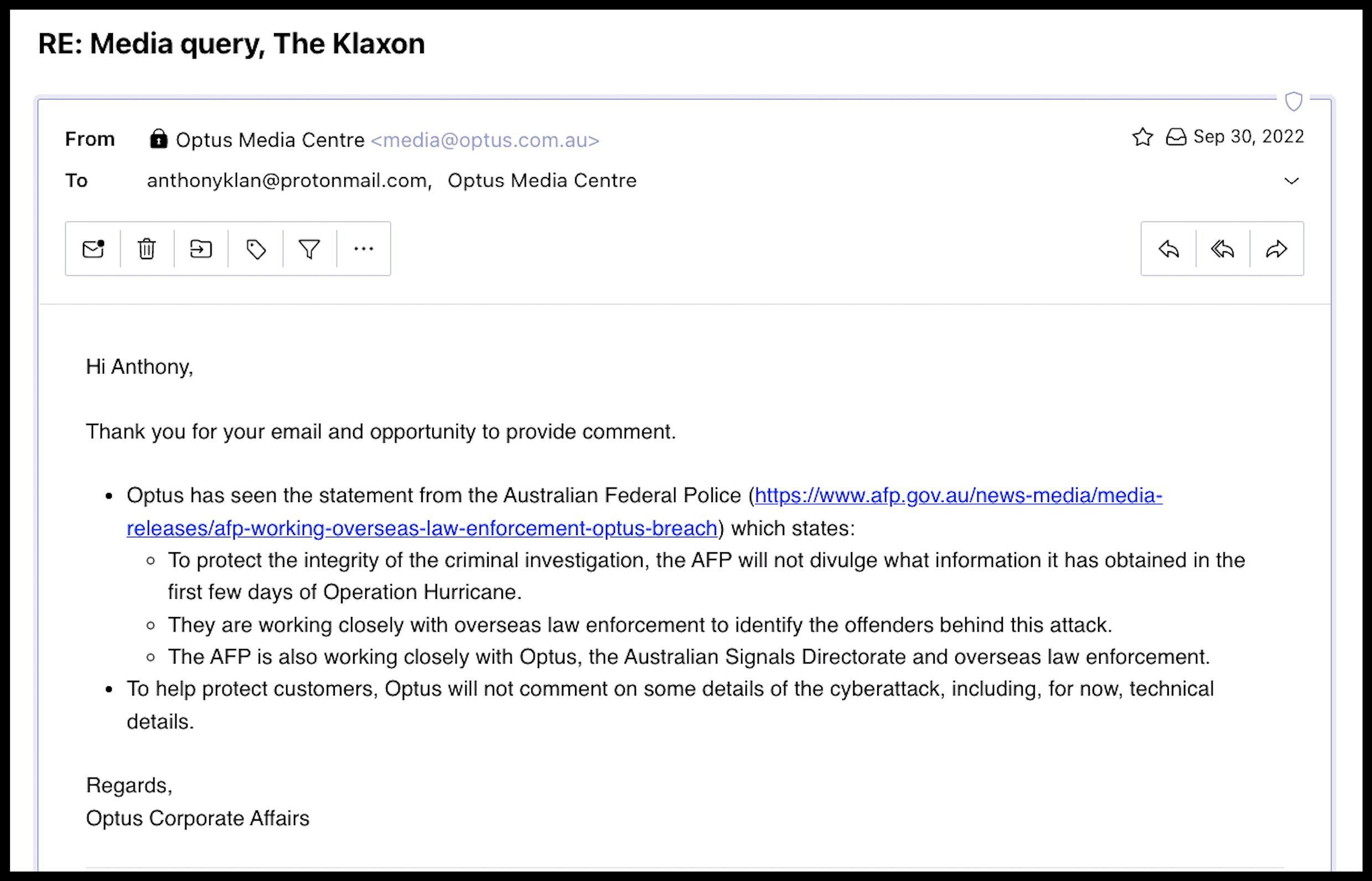
Remarkably – and despite being heavily admonished by the Australian Government for lack of communication – Optus and its CEO Kelly Bayer Rosmarin repeatedly refused to comment when asked whether Trustwave was used to protect Optus’ Australian customers.
On Wednesday September 28, and again on Friday September 30, The Klaxon put the question to Bayer Rosmarin and Optus.
We also asked that if Trustwave, Optus’s “global cybersecurity leader”, was not in charge of protecting the cybersecurity of Optus’s almost 11m Australian consumer customers, then who was.
Bayer Rosmarin and Optus did not answer our questions, instead providing a generalised statement saying the group was “working closely” with authorities.
Trustwave:
- “Global security arm of Singtel, Optus and NCS”
- 2,000+ “security-minder employees worldwide”
- 200,000+ “business and government customers”
- 5,000+ “enterprise managed security services clients”
- “Global Trustwave customer footprint” in 96 countries
- 9 “security Operations Centres”
Trustwave is headquartered in the US, suggesting a reason for the involvement of the US Federal Bureau of Investigation (FBI), announced days after the breach emerged.
The FBI is the domestic intelligence arm of the US.
Trustwave’s “worldwide headquarters” are in Chicago. It also has offices in three other US states as well as in five other countries.
(Days before the FBI’s involvement was announced, Rosemarin said it was a “sophisticated attack” and that it was “safe to say it comes out of various countries in Europe”.)
“We are cyber defenders”. Source: Trustwave
Trustwave says it has a “ global team of security professionals” comprised of “2,000-plus security-minded employees worldwide” who are “solely dedicated to protecting businesses” including “5,000-plus enterprise managed security services clients”.
Its “elite cybersecurity expertise” is “found nowhere else in the industry”, Trustwave says.
It provides the “largest breadth and depth of managed security services available from a single provider anywhere” and is “one of the most experienced, fastest growing MSSPs (managed security service providers) in the world”.
“Eradicate cyberthreats with world-class intel and expertise”. Source: Trustwave
Both the Australian Government – which installed its top cybersecurity agency immediately after the mass breach emerged – and the Federal Opposition have heavily admonished Optus.
Australia’s Cyber Security and Home Affairs Minister Clare O’Neil has said the “unprecedented” breach was a “simple hack”.
Australian Prime Minister Anthony Albanese said it was the biggest data breach in the nation’s history and should “have never had happened”.
James Paterson, Shadow Minister for Cybersecurity and Shadow Minister for Countering Foreign Interference, said Optus “absolutely” deserved that criticism.
“They did not have in place sufficient protections to protect the data of almost 10 million Australians that they were holding,” Paterson said.
The Australian Government’s top cybersecurity agency is the Australian Cyber Security Centre (ACSC).
It is part of the Australian Signals Directorate (ASD) and based within the Canberra headquarters of the Australian Security Intelligence Organisation (ASIO), the nation’s domestic intelligence agency.
“What is of concern for us is how what is quite a basic hack was undertaken on Optus,” O’Neil told ABC’s 7.30 on September 26.
“We should not have a telecommunications provider in this country which has effectively left the window open for data of this nature to be stolen”.
“We should not have a telecommunications provider in this country which has effectively left the window open for data of this nature to be stolen” – Cyber Security Minister Clare O’Neil
Since then, O’Neil and other government ministers have repeatedly and consistently confirmed that position.
The Australian Cyber Security Centre (ACSC) was involved immediately, “supporting Optus with a cybersecurity incident response”.
“Optus is working with the Australian Cyber Security Centre,” Optus said in its statement announcing the data breach on September 22.
Last Sunday O’Neil said the cyber security agencies had now completed their “technical work” with Optus.
“I spoke this morning with the heads of the Australian Signals directorate and the Australian Cyber Securities Centre, these are the government agencies which contain cyber security expertise within the Australian Government,” O’Neil said.
“They have advised me that they have completed the technical work that they have been doing with Optus”.
Optus CEO Kelly Bayer Rosmarin has said the breach “should not have happened”.
Yet she has claimed – repeatedly and consistently – that it was a “sophisticated” breach, directly opposing the findings of the Australian Government and its intelligence and cybersecurity agencies.
The Klaxon has been unable to find any IT or cybersecurity experts who back Bayer Rosmarin’s version of events.
The Klaxon has been unable to find any experts who back Bayer Rosmarin’s version of events.
ACS is the peak professional body for Australia’s tech sector with over 35,000 members.
Louay Ghashash, chair of the ACS Cybersecurity Advisory Board, said “heads should roll”.
“A breach of that size should see heads roll. That’s when they will start listening, and they will start taking this seriously,” Ghashash said.
Vice chair of the ACS Cybersecurity Advisory Board Joseph Dalessandro, said: “If you’re an IT director of a company of any size, and you’ve had a large outbreak of malware where your company can’t recover, can’t do business, and can’t restore data – you are a moron and should be fired”.
“You are a moron and should be fired” – Joseph Dalessandro
Notably, Trustwave has made no comment since the scandal emerged.
Optus is Australia’s second biggest wireless carrier and has been owned by the Singapore Government-controlled Singapore Telecommunications Ltd, or Singtel, since 2001.
Singtel’s chair is Lee Theng Kiat, who is also a director of Temasek, which is the Singaporean Government sovereign wealth fund that controls and majority-owns Singtel.

Singtel chair Lee Theng Kiat. Source: Singtel
In the year to March 31, Singtel reported revenue of S$15.34bn ($16.83bn).
It reported a profit of S$3.77bn ($4.13bn), of which more than half, $1.927bn ($2.11bn), came from its “Australian consumer” business.
Trust waive?
The scandal engulfing Optus – and the central question of whether Australian consumers were protected by Trustwave – comes as Singtel quietly moves to try and sell the asset.
On August 22, four weeks before the breach emerged, Bloomberg reported Singtel was “speaking with financial advisers” shopping Trustwave around.
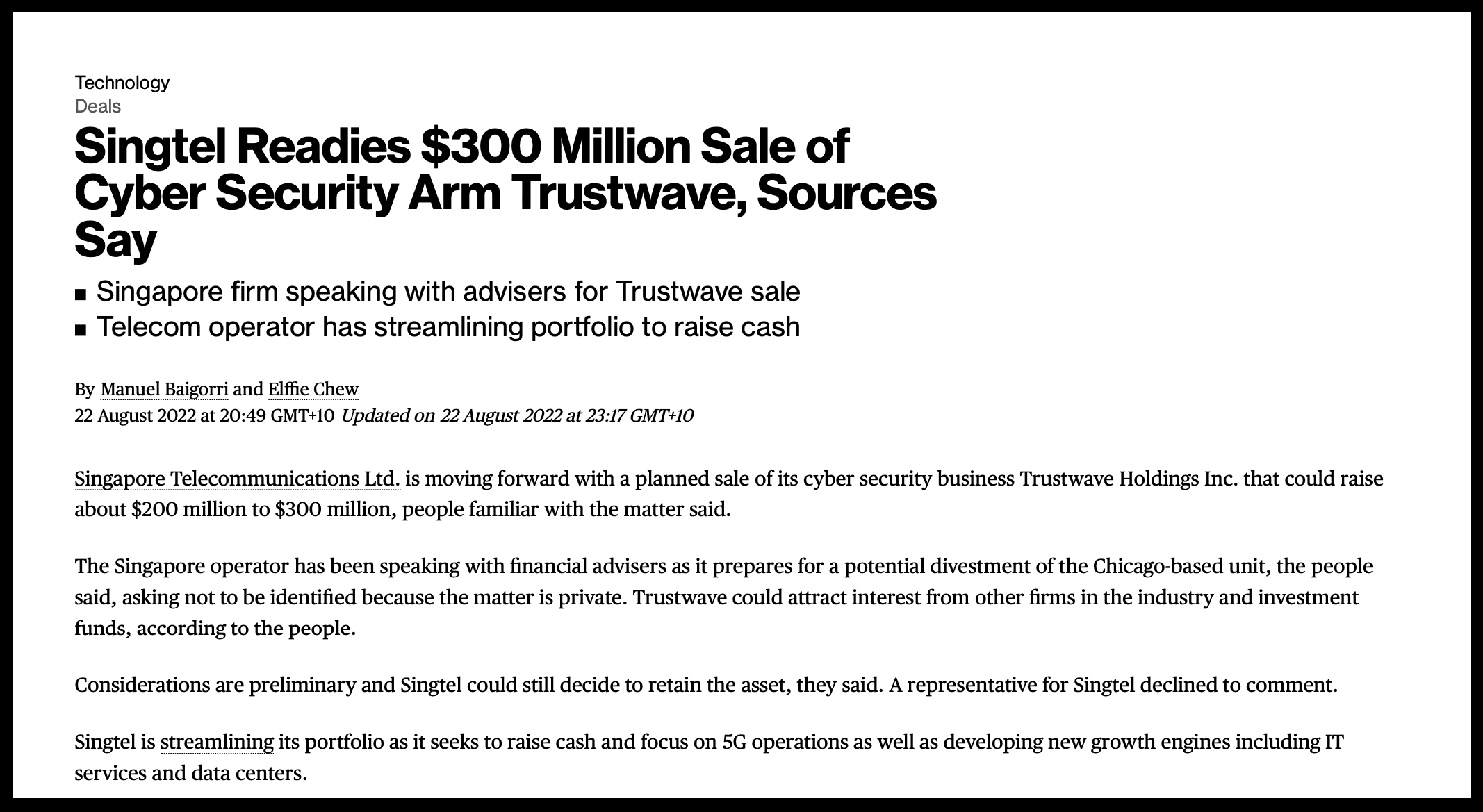
Singtel reportedly preparing to sell Trustwave. Source: Bloomberg
That planned sale makes the issue of whether or not Optus retail customers were ostensibly protected by Trustwave particularly important.
Bloomberg reported Singtel was seeking “between US$200m and US$300m” ($308m – $461m) for Trustwave.
Former head of the Australian Cyber Security Centre, Alastair MacGibbon, told The Sydney Morning Herald it “appears to be the consensus” that the breach was “quite simple” and “not sophisticated”.
MacGibbon, who is now chief strategy officer at private firm CyberCX, was the founding head of the Australian Cyber Security Centre, a position he held until 2019.
He was Australia’s inaugural eSafety Commissioner and formerly National Security Advisor and Special Advisor to the Prime Minister on Cyber Security.

Former and founding head of the Australian Cyber Security Centre, Alastair MacGibbon. Source: Supplied
The Sydney Morning Herald writes: “Several industry insiders, who spoke anonymously because their employers had not authorised them to speak, said such a lapse should never have happened. They argued it fit Optus’ reputation for having a stingy approach to cybersecurity, which generates no money for businesses.”
Whether or not Optus was using Trustwave to protect its Australian customers will likely carry serious consequences.
The Telecommunications Act states carriers and carriage service providers must “do their best” to protect telecommunications networks from unauthorised access.
Information and Privacy Commissioner Angelene Falk has said she wants to know “what security was in place”.
“I’m seeking information about what security was in place at the time that this breach occurred,” Falk told ABC’s 7.30 last Monday.
“I’m seeking information about what security was in place at the time that this breach occurred” – Angelene Falk
“I will assess that information and decide whether further regulatory action is warranted.”
Falk, nor anyone else in government, has made any mention of Trustwave.
Questions The Klaxon put to Bayer Rosmarin and Optus on Sep 28 and Sep 30:
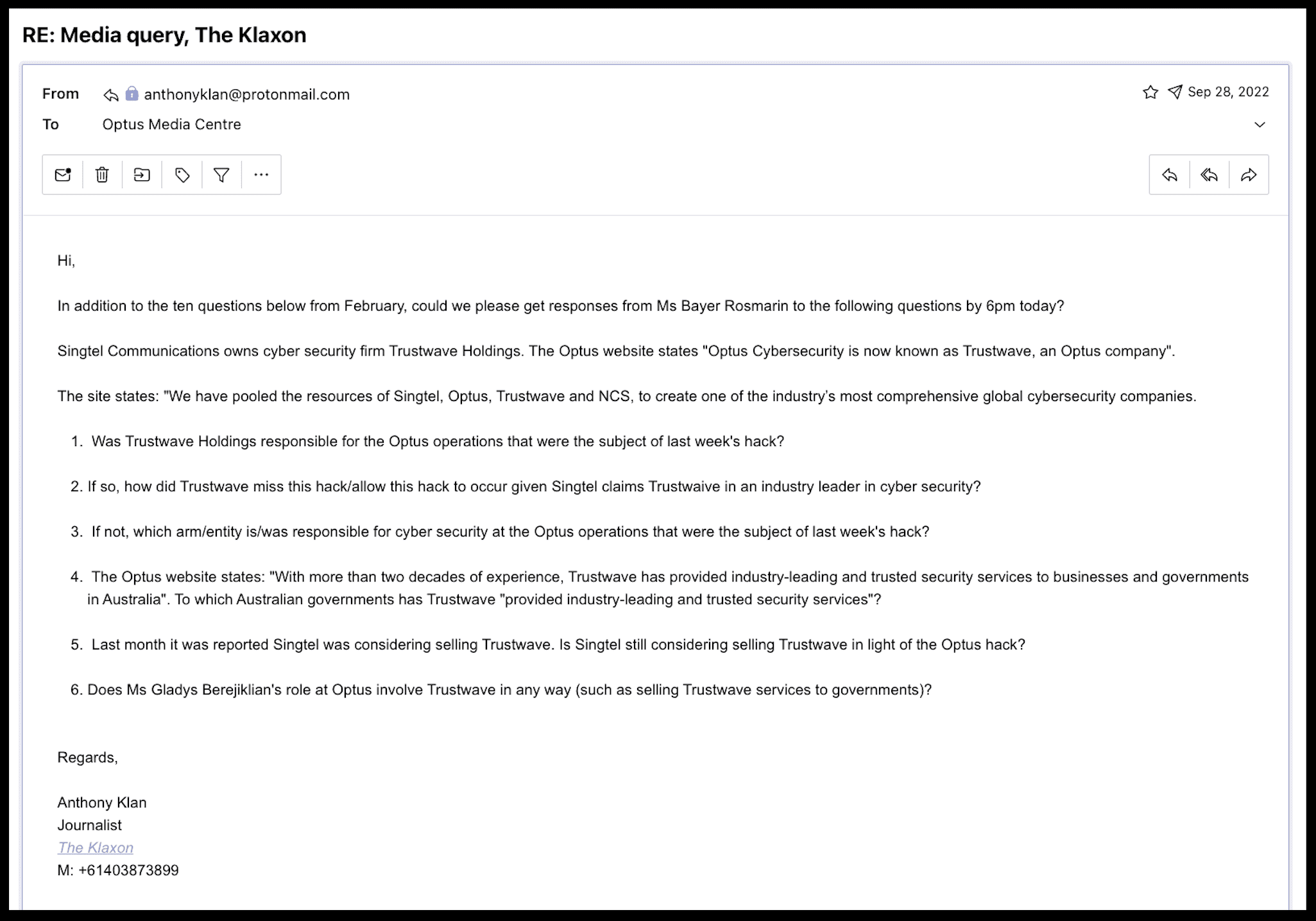
Optus’ response:
If Optus was not using Trustwave, or not using Trustwave to its full extent, it will likely bolster the case for a class action, which some experts say would already “easily be Australia’s biggest” and could cost the telco “billions”.
That Optus runs a “global cybersecurity leader” – but is refusing to say whether it was using it to protect its own customers – brings further into question Bayer Rosmarin’s announcement last Monday that she had appointed consultancy firm Deloitte to conduct a “review” of what she calls a “cyberattack”.
Many experts view the announcement – which came hours after she and Optus were admonished by both O’Neil and Government Services Minister Bill Shorten over failing to government with key data – as a cynical ploy to buy time in the hope the scandal blows over, with Bayer’s future as CEO in serious doubt.
Optus has come under fire for saying it won’t release the findings of the Deloitte investigation, citing “security”.
On Monday last week The Klaxon asked Optus which arm of Deloitte and from which country was it conducting the “investigation”; who at Deloitte was responsible for overseeing it; whether its findings would be released; how long it was expected to take; and the specific “terms of reference” that Optus had set for Deloitte’s investigation.
Optus said it would “not be releasing some findings” citing “security”.
Optus provided no other answers, other than to say: “In regards to your questions around Deloitte, as this is an independent review these are a matter for Deloitte to decide”.
Unlike Singtel and Optus with Trustwave, Deloitte does not own or operate any substantial cybersecurity business.
“Trustwave, an Optus company” is a “global cybersecurity leader”. Source: Optus
Trustwave’s website says its “award-winning”, “elite team” specifically “covers the entire lifecycle of a security incidence”.
Its “security breach investigations” had established Trustwave “as world-renowned experts on the past, present and future of security”.
“Trustwave covers the entire life-cycle of a security incidence – from initial detection through returning a network back to steady state operation – all under one roof by a global team of security professionals solely dedicated to protecting businesses,” it says.
Rosemarin and Optus’s governance arrangements have already come under serious scrutiny this year, after Bayer Rosemarin announced in February she had appointed former NSW Premier Gladys Berejiklian, to a senior role.
“I believe she will be a game-changer for Optus…under this newly created role,” Bayer Rosemarin said.
Berejiklian resigned as Premier of NSW – Australia’s biggest state – in October last year after the NSW Independent Commission Against Corruption (ICAC) said she was one of two people under investigation in a corruption probe.
Operation Keppel, which is also investigating disgraced former NSW MP Daryl Maguire, Berejiklian’s former partner, remains a “current investigation” and is yet to make its findings.

Shorten and O’Neil press conference, October 2. Source: Supplied
On Sunday October 2 O’Neil and Government Services minister Bill Shorten held a joint media conference to raise their ongoing serious concerns that Optus was failing to cooperate with government and not providing critical information including regarding customers whose Medicare details had been exposed.
What Optus was doing was “not enough”, Shorten said.
“We need this, not tomorrow or the next day, we really needed it days ago.
“It’s been 11 days since the breach.”
Optus hit back through the media on Monday, stating it had been working towards a provided deadline of October 4 to provide Government arm Services Australia with certain information.
Shorten’s issued a direct response.
“I’m pleased that our Service Australia people were able to get data finally today but…senior management are kidding themselves if they want a medal for the way that they’ve been communicating,” Shorten said on Tuesday.
“Even a crocodile wouldn’t swallow that.”
Optus’ regulatory and public affairs team is overseen by Berejiklian.
Coming soon: Part Two
WE HAVE A FAVOUR TO ASK: We receive zero government funding and are entirely funded by our readers. Investigations such as this take an enormous amount of time and effort. Our financial position is currently extremely tight. If you appreciated this article, and our high-quality investigative journalism, please DONATE HERE to help keep us afloat. Thank you very much for your support.
Anthony Klan,
Editor The Klaxon
Do you know more? anthonyklan@protonmail.com
Help us get the truth out from as little as $10/month.
Unleash the excitement of playing your favorite casino games from the comfort of your own home or on the go. With real money online casinos in South Africa, the possibilities are endless. Whether you’re into classic slots, progressive jackpots, or live dealer games, you’ll find it all at your fingertips. Join the millions of players enjoying the thrill of real money gambling and see if today is your lucky day!
The need for fearless, independent media has never been greater. Journalism is on its knees – and the media landscape is riddled with vested interests. Please consider subscribing for as little as $10 a month to help us keep holding the powerful to account.






